Secure Authentication to your network
Many users in an organization struggle to maintain and manage their own credentials. 90% of the users still use username and password to log in their applications and platforms. Even with the use of Multi-Factor Authentication (MFA), hackers still find ways to steel credentials with their new techniques.
This page describes how passwordless access and managing passwords, devices and identity in a central repository can help you to offer secure access, for every user, from whatever place, from any device to any application they are entitled to.
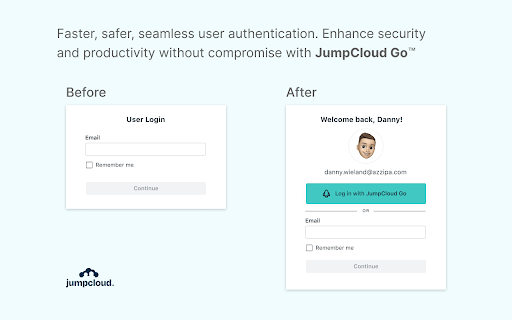
Identity Management
User identity can be stored in different sources like Entra ID, local AD, Google Workspace or alternative IDP sources. The more differentiated the environment, the more complex it get for system administrators to manage, to provision or to de-provision users with acces to your network and applications
Mobile Device Management
Mobile Device Management (MDM) allows you to centrally manage your cross platform (Windows, MacOS, iOS, Android & Linux) devices with unified security policies. Whether you use your Bring Your Own Device (BYOD) or corporate own devices, we discuss here how you can ensure secure access from anywhere, no matter the device, to the right applications.
Automated user provisioning
Within complex environments, with the use of IDP sources like Entra ID/Google Workspace or local AD sources, it can be complex to offboard or onboard employees. We shown you on this page how you can automate user provisioning with the right set of rights to the applications that they’re entitled to, next to easily onboard and offboard employees in a central way.
Identity Access Management (IAM)
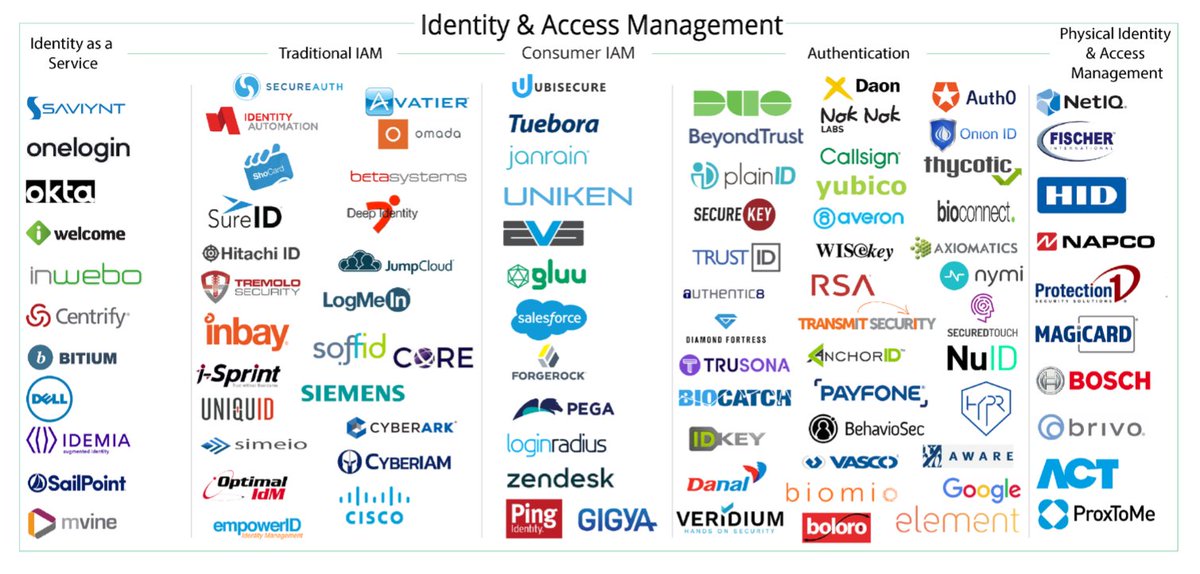
Identity Access Management knows a lot of suppliers that offer their applications for managing the identity of users in organizations. A lot of them use Microsoft Entra ID, but Google Workspace, Okta, One Identity, Ping identity might be possible as well.
What if you are using different Identity Sources?
When companies are merging, or get acquired by others, Identity management can get really complex and time consuming for IT managers to manage identities.
Can you imagine that you need to login in each management console of every Identity Provider to manage the user roles of the different employees?
Time and license cost of different tools
When using different IAM solutions in one environment can cause higher time consumption of administrators, higher license cost of these tools and less efficiency in onboarding and offboarding of new employees.
From a dozen till hundreds of tools to manage
-
Large Enterprises:Forrester Consulting found that large enterprises use an average of 367 software applications and systems. SaaS management statistics from Productiv also shows that the average SaaS portfolio contains 315 apps, with teams using 50-70 SaaS apps.
-
Smaller Businesses:While the exact numbers vary, smaller businesses will generally have fewer applications to manage than large enterprises. However, even with a smaller number, managing these tools effectively can be challenging, especially with the rise of shadow IT.
-
Shadow IT:A significant challenge for IT managers is the prevalence of shadow IT, where employees use unapproved software. According to a G2 study, 80% of workers admit to using SaaS applications without IT approval, and the estimated size of shadow IT cloud usage can be 10 times the size of known cloud usage.
-
Project Management Tools:A single organization might use multiple project management tools, with one study indicating an average of 11 different tools per organization, leading to potential redundancy and communication challenges.
- IT Staffing Ratios:
Atera suggests that organizations with over 7,000 employees should have a 1:100 or 1:200 IT staffing ratio, indicating a significant responsibility for managing software within IT departments.
Management of all these tools is not only time consuming but as well not budget friendly when you consider all the licenses and cost they carry.
One Centralised Identity Management Console
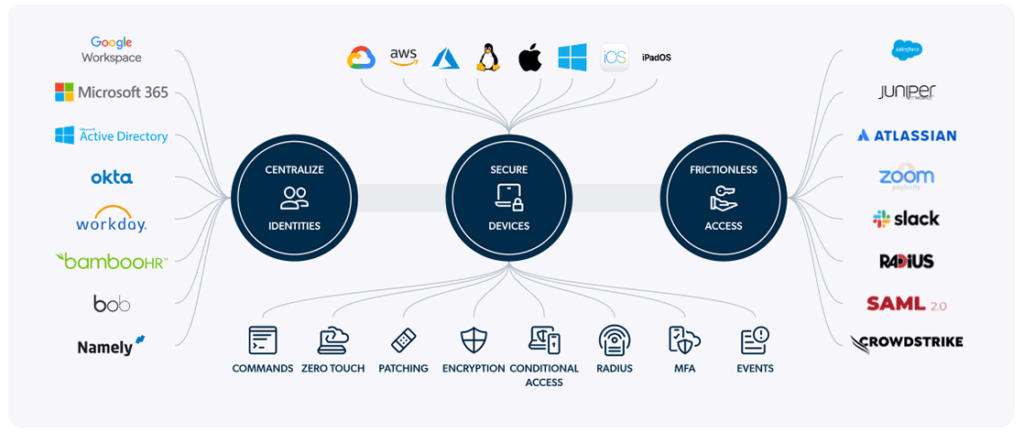
What if you use one central Cloud Identity directory that is connected to all Identity providers you use in your organization?
JumpCloud can help you to centralize the Identity database that connects your existing Identity Sources like Entra ID, Google Workspace or others, with the JumpCloud Central Directory in a bi-directional way.
Bi-directional automation of different identity sources
When the JumpCloud Cloud Directory is used to centralize all identities of users, coming from Entra ID, Google Workspace, Local AD, and has bi-directional functionalities is becomes possible to manage identities from central repository and update immediately the source of origin with the made changes.
Organizing users in different groups
When you have collected all the user identities in the central repository of JumpCloud you can create different user groups, like :
- Sales
- Marketing
- Support
- IT
- IT-Admin
- Finance
- …
You can apply different authentication rights to each group made and provision them with the right set of applications.
Password Management
When the most of the users are using the traditional way of password management, username and password, it is essential that passwords are collected in a central and decentralized way. When having only one vault, the risk of a data leak during a hack of all passwords are quite high.
What if the storage of passwords are organized in a de-centralized way?
JumpCloud Go can be used on your device where your password is stored locally on the device, but optional the cloud repository. When the central vault is compromised, passwords can be reset locally on every device.
Passwordless Authentication
Multi-Factor Authentication (MFA) and passwords are no longer for 100% safe due to several know hacking techniques for bypassing MFA.
This is the reason why Kappa Data advices to use Passwordless Access from your device to your application.
Passwordless Access with JumpCloud
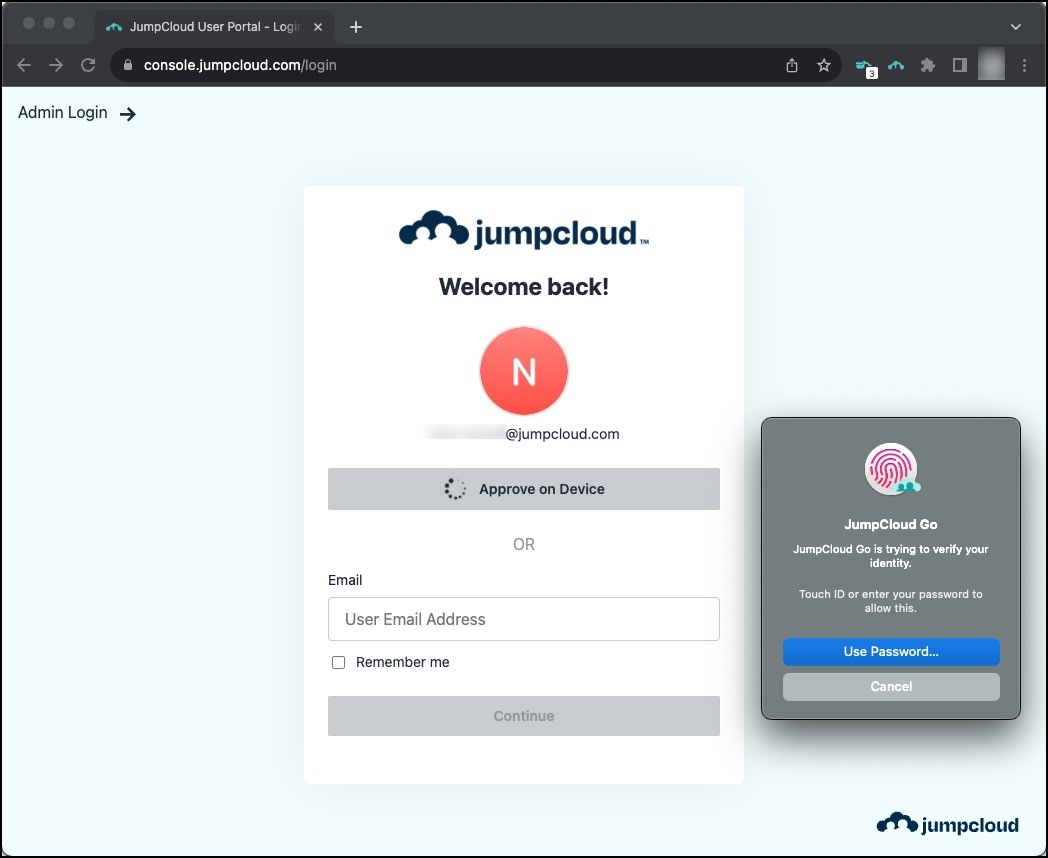
With JumpCloud Go, the agent installed on your device(s) allow to click on a button to connect to your environment. With JumpCloud Go it is even possible to activate a two-factor authentication with the use of your fingers or face-ID to login with the incorporated FIDO2 standard, like available on MAC computers. .
Passwordless Authentication with OneSpan FIDO2 tokens

Whenever you don’t have an Apple device or using the biometrics of Windows Hello, Kappa Data can offer you the possibility of a FIDO 2 token of OneSpan.
These tokens are personal, and can be used by the employee to logon towards business applications but as well private applications in their time.
More information about these tokens can be found on : FIDO2 tokens by OneSpan
Identity Device Management
Next to Identity Access Management of users in one central cloud directory, Kappa Data offers with JumpCloud the ability to manage devices from the same cloud directory.
Devices are as well grouped in several groups per operating system and bound to the users:
- Windows
- MacOS
- Linux
- iOS
- Android
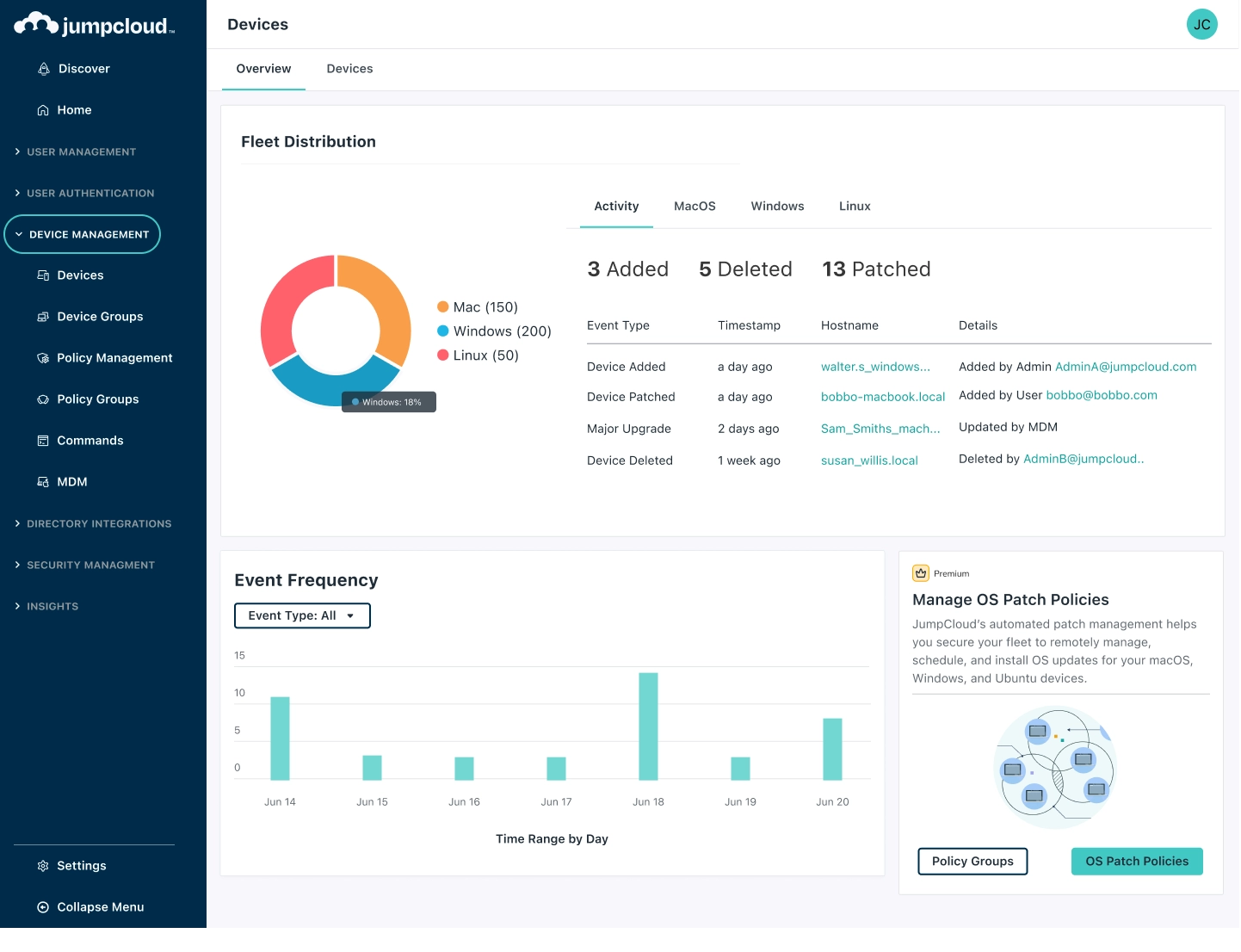
Within Device Management you are able to create policies and apply them to the devices or apply policy groups to the right device group that you have defined.
Enrollment of new devices can be automated and commands can be pushed.
More information can be found on our page Mobile Device Management
Contact us for a demo
Are you curious to learn how we can help you to improve and control authentication to your network? Contact us for a demo via the below button.
