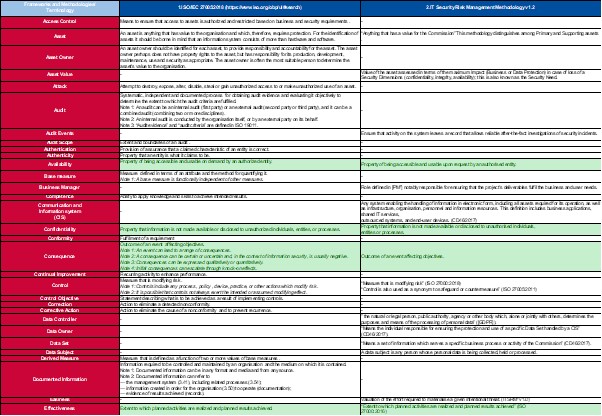
Asset Discovery with runZero
runZero brings a new form of asset discovery to map devices within an IT, IoT to even an OT environment. Thanks to new techniques, 30-40% more devices in the network are discovered without the use of an agent on the device. Find out all about it here.
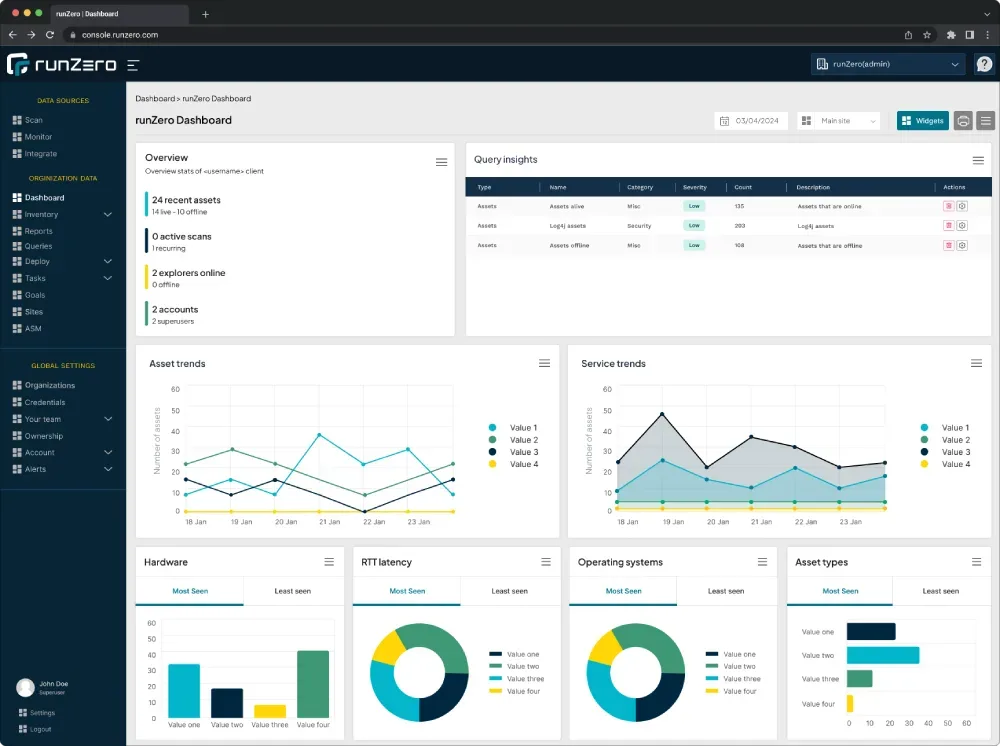
Importance of Asset Discovery in NIS2
With the forthcoming regulations around NIS2 in the Netherlands in mind, these regulations expect an Asset inventory to perform a risk analysis on this. For organisations within traditional IT environments, it is relatively easy to list the number of laptops, servers, smartphones and printers. But what do you do with Video IP cameras, electric charging stations or temperature sensors in server rooms. Often, these elements are also forgotten.
Within OT environments (e.g. manufacturing), the problem set is sometimes even greater. Often, within these critical environments, specific devices are used on which no scanning software can/may run.
As a network administrator, how will you manage these devices and detect any problems?
A new way of Asset Discovery with runZero
Achieve complete, unified asset inventory and superior attack surface management.
runZero is a cyber asset attack surface management (CAASM) solution that enables security teams to gain comprehensive visibility into complex environments and accelerate exposure management.
With a unique combination of active scanning, passive detection and integrations, runZero discovers all IT, OT and IoT assets anywhere: on-premises, in the cloud and externally. With runZero, you can:
- Achieve a comprehensive asset inventory in a single platform
- Securely detect unknown devices and networks
- Identify each device in detail
- Visualise network topology and segmentation issues
- Continuously monitor your internal and external attack surfaces
- Quickly identify missing security measures
- Identify and prioritise exposures that may pose a risk

Get stunningly detailed information on every device.
Importantly for security, a Linux device is an IP camera and not a laptop. runZero has patented fingerprinting capabilities that provide in-depth details and insights about operating systems, services, hardware and more.
Fingerprinting

Identify unauthorised services and see which protocols are used.
Importantly for security, a Linux device is an IP camera and not a laptop. runZero has patented fingerprinting capabilities that provide in-depth details and insights about operating systems, services, hardware and more.
Services

See what runs where and inventory your apps
Importantly for security, a Linux device is an IP camera and not a laptop. runZero has patented fingerprinting capabilities that provide in-depth details and insights about operating systems, services, hardware and more.
Software

Close gaps in EDR coverage and improve security measures.
Endpoint protection
Ensure critical assets are scanned for vulnerabilities.
Scan vulnerabilities

Know who is responsible for each asset.
Ownership of assets

Understand your attack surfaces inside and out.
Attack surface assessment

Visualise network topology and segmentation.
Network insights
Explore unknown subnets safely and easily.
Unknown subnets

Safely discover even the most vulnerable devices.
OT Support

Collect, correlate and deduplicate data from multiple sources.
Data Unification

Make sure your CMDB and SIEM are accurate.
Seamless integration
Meet the Gartner Peer Insights ‘Customers’ Choice’ for CAASM.
Achieve full security visibility and discover vulnerabilities within minutes.
Platform Overview
runZero provides the fastest and most complete security visibility across your assets and internal and external attack surfaces, allowing you to mitigate vulnerabilities before they are exploited – while remaining compliant with regulations.
Exposure limitation
runZero allows you to quickly find emerging threats in your environment without rescanning, identify and prioritise vulnerabilities, and perform automated outlier analysis. Need help removing EOL software? We help with that too.
Risk and compliance
runZero meets the requirements for maintaining a complete asset inventory, continuously monitoring attack surfaces and verifying security measures. In addition, the platform accelerates discovery and risk analysis in mergers, acquisitions and divestments.
Results in minutes
runZero is quick and easy to use. You don’t need logins or agents, and no expensive devices are required. We also offer flexible deployment options, including SaaS and on-premises, and we support closed environments.
Frequently asked questions
Check our FAQ section where you can find the first questions that have been asked to us during the last months.
Contact usHow does runZero assist in vulnerability management as required by NIS2?
runZero plays a critical role in helping organizations meet the vulnerability management requirements of the NIS2 Directive by providing comprehensive asset visibility, risk detection, and integration with existing security workflows. NIS2 emphasizes proactive cybersecurity measures, including identifying, assessing, and mitigating vulnerabilities across IT and OT systems — a core capability of runZero.
How does runZero enhance asset visibility and management?
runZero enhances asset visibility and management by delivering comprehensive, real-time discovery of all connected devices—without requiring agents or credentials. It enables organizations to gain a complete and actionable inventory of their IT, IoT, and OT environments, which is essential for security, compliance, and operational efficiency.
How does runZero help organizations comply with the NIS2 directive’s asset management requirements?
runZero helps organizations comply with the NIS2 Directive’s asset management requirements by delivering real-time, accurate, and comprehensive asset visibility—a foundational need for meeting NIS2’s focus on cybersecurity risk management, operational resilience, and accountability. runZero uses agentless active scanning and passive discovery to identify all connected assets like IT, IoT and OT devices, connected to your networks
How does runZero support the overall security strategy required by the NIS2 directive?
runZero supports the overall security strategy required by the NIS2 Directive by delivering foundational capabilities in asset discovery, risk management, threat detection, and incident preparedness. These align directly with NIS2’s goals of improving cyber resilience, ensuring risk-based security, and enhancing situational awareness across critical and essential sectors.
Why is asset management important for cybersecurity?
Asset management is crucial for cybersecurity because it enables organizations to identify, track, and manage all devices and systems connected to their network. Knowing what assets are present allows for effective vulnerability management, ensures that security policies are enforced consistently, and reduces the risk of unauthorized devices accessing the network.
Why is continuous asset discovery and inventory management critical for NIS2 compliance?
Continuous asset discovery and inventory management are critical for NIS2 compliance because they ensure that the organization’s asset inventory is always accurate and up-to-date. This is crucial for identifying unauthorized devices, assessing security risks, and implementing effective controls to protect critical infrastructure, all of which are mandated by the NIS2 directive.
Why is real-time asset monitoring essential for compliance with the NIS2 directive?
Real-time asset monitoring is essential for compliance with the NIS2 directive because it ensures that any changes in the network environment, such as the addition of new devices or changes in device behavior, are immediately detected and addressed. The NIS2 directive emphasizes the importance of maintaining an up-to-date view of the network and its assets to respond quickly to potential security incidents.
Contact us for a demo
Are you curious to learn whether how runZero can help you with searching of assets in the network and how to protect these assets? Contact us for a demo via the below button.